 WordPress is the most popular web publishing platform. It is also open-source, which results to a huge, lively community that tweaks, adds functionalities and fixes bugs. However, WordPress popularity also means another thing: it is a prime target for hackers. Whenever a vulnerability is discovered on WordPress, it will be exploited.
WordPress is the most popular web publishing platform. It is also open-source, which results to a huge, lively community that tweaks, adds functionalities and fixes bugs. However, WordPress popularity also means another thing: it is a prime target for hackers. Whenever a vulnerability is discovered on WordPress, it will be exploited.
WordPress developers are doing their best to keep the core WordPress installation as secure as possible. However, a number of vulnerabilities come with each release of a new WordPress version, as it is outlined in this article on WP White Security. Furthermore, adding plugins and themes on a clean WP installation add new layers of possible vulnerability.
In this article, we will present some simple, actionable ways of things that you can do right now to harden your WordPress site’s security. Please keep in mind that, if your site is compromised, you should contact a security specialist to take the necessary measures to solve the problem and harden your website. These simple tips are not meant to completely replace a well-thought out security plan.
The easy part.
1) Always have the latest version of WordPress installed
This is the most important thing you can do to keep your website safe. Hackers target installations with known vulnerabilities. The development team of WordPress strives to patch every vulnerability that comes into their attention and each release is more secure than the previous one.
2) Use of strong passwords
When you install a new WordPress blog, on one of the installation screens, you are asked to configure the administrator user’s password.
WordPress has a password generator, that chooses a strong password for you. Does it look unpronounceable, does it have symbols like %$#-, etc, a mix of numbers, lowercase and uppercase letters? Great, this is a strong password. A hacker cannot guess it by using a dictionary, or by knowing some basic information about you.
On that note, it is a good idea to make sure that your administrator user’s username is not “admin“. Many hosts offer an one-click installation of WordPress and they choose both administrator’s username and password for you; they usually assign the default username “admin“.
If this is the case, please consider creating a new admin user with a more complex username, and delete the old one.
3) Make use of user permissions.
WordPress implements user roles and permissions, according to the Principle of Least Priviledge. In our previous point, we recommended to change the default admin username. To expand on this: create a separate user to update your content and write articles. Do not use your administrator user for anything else than strictly administrative purposes: updating WordPress and themes, installing or uninstalling plugins, or other maintenance – administrative tasks.
4) Hide your login URL.
Up to now, we have created a user with admin capabilities that does not have the default “admin” username and has a strong password. To take this one step further: let’s hide the default, www.mywebsite.com/wp-admin/ login URL.
The simplest way to do this is by using a plugin, called WPS Hide Login.

Install this plugin and you can rename your login page to anything you want.
5) Further secure your login URL.
This is an additional step, recommended by WordPress documentation. Use a server side protection layer, requesting a password to even access the login URL and the WordPress core files.
WordPress codex recommends a tutorial in WP Beginner, that explains step-by-step how to password protect your wp-admin directory.
It is also worth considering to add a captcha, in deny access to your login page to bots and automated scripts. The simplest possible plugin to achieve this is Login No Captcha reCAPTCHA: by adding a simple check box to your login page, it can be useful to weed out many automated scripts.

For a more comprehensive approach, Google Captcha (reCAPTCHA) by BestWebSoft is a great solution. It can be used with any form, not only in the login screen and it makes it extremely hard for bots to submit form information.
The hands-on part
For the following few recommendations, there is a little bit of code editing. You will need to have access to your WordPress core files to edit. Please, always backup your files first, before editing.
6) Hide some information about your site.
As we already said, WordPress developers do their absolutely best to hand over a secure, bugs-free product, however, there always are some vulnerabilities in each WordPress version. A potential hacker, can see your WordPress version by visiting your page and examining the page source; then, they can search the vulnerabilities and potential exploits attached to your WordPress version and plan their attack.
You should consider hiding the exact WordPress version you are using. To do this you need access to the functions.php file of your theme, usually located in the <www.yoursite.com>/wp-content/themes/<your-theme-name>/functions.php, accessible or via FTP or, (for the moment, at least, if you read the following suggestions), via the theme editor.
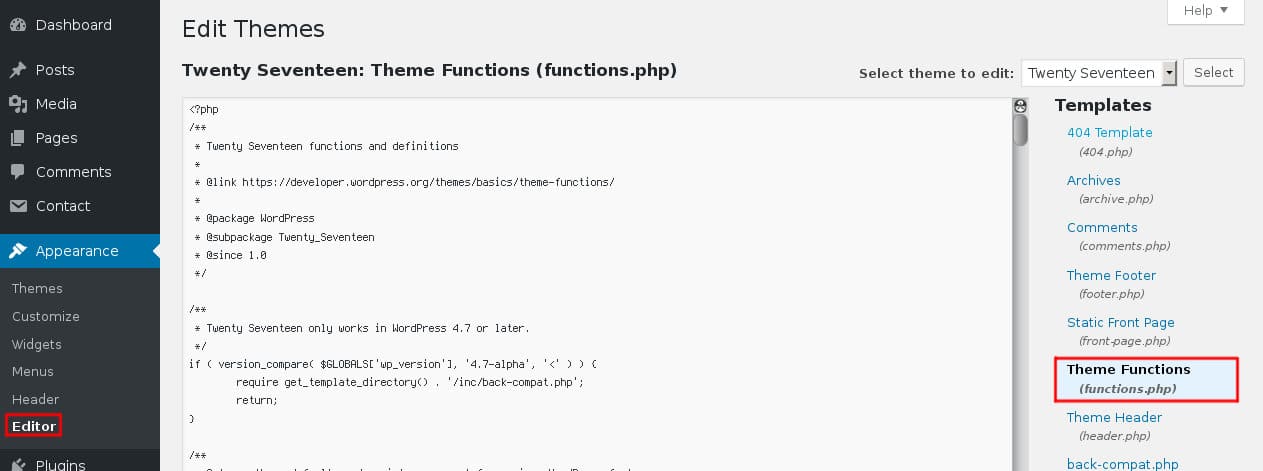
Simply add this line:
remove_action('wp_head', 'wp_generator');
… and this removes the string that reveals your WordPress version in the page header.
While we are still on the functions.php of our theme, let’s also hide the “Windows Live Writer” link from our page header. Unless you are actually using Windows Live Writer, there’s no good reason to keep this link:
remove_action('wp_head', 'wlwmanifest_link');
7) WordPress core files – “README.HTML”
After a fresh WordPress installation, there are a few files in your installation directory that, while they are of no use to you whatsoever, they can give valuable information to a malicious attacker scanning for vulnerabilities.
The first of those is the readme.html file, on the top level of your WordPress directory. If anyone can simply append readme.html at the end of your website’s URL and access a web page with your WordPress version information, then hiding the WordPress version in the header, in the previous step, was for nothing.
Simply renaming the file to something non-intuitive, example rename to “readme-8345nfrj435.html` is enough to take care of this.
8) WordPress core files – “INSTALL.PHP” and “UPGRADE.PHP”
The following two WordPress files, install.php and upgrade.php reside in your wp-admin folder and they can be a security hole in your installation.
The install.php file has only one purpose: to guide you to the “WordPress 5 minutes installation”. After you have completed your installation, there is absolutely no reason to keep this file. You should simply delete it. At the very least, we recommend that you rename it to something not easy to guess, like for example install-5735435.php.
The upgrade.php is a file you should not delete, as it can be useful; however it provides a script to upgrade your whole WordPress database and, as such, it should not be accessible in its default location in wp-admin. We recommend, for this file too, to rename it to something not easy to guess, like upgrade-987UIUI.php.
9) Remove the Plugin and Theme Editor.
Any developer knows how handy it is to be able to edit theme or plugin files directly from the dashboard. We also made use of the Theme editor in the step 6 of this guide, where we edited our theme’s functions.php file.
However, once your website is out of the development stage, there is no reason to give an easy way to a potential hacker to take down your entire site by just modifying one or two lines of code. There is also no reason to allow your authorized users to do changes by mistake.
To do this, we will have to edit a WordPress core file, the wp-config.php file, located on the top directory of our installation. Please don’t forget to take a backup copy of your wp-config.php file!!!
The line to add is:
## Disable Editing in Dashboard
define( 'DISALLOW_FILE_EDIT', true );
10) Backup!
Yes, keeping backups is not exactly a security tip, however you should keep up-to-date backups of your wp-content directory, as well as of all your posts and pages. In a previous article we have described an easy way to backup your whole WordPress installation using a plugin.
All the above tips will help harden a bit your WordPress installation; the majority of hackers are after easier targets, with old WordPress versions, old and vulnerable plugins and themes, and sites with easy to guess or to brute-force login credentials. The above tips will take you just a step above the majority of vulnerable WP sites; however a dedicated hacker who actually wants to harm you and your site, might actually manage it and cause you damage. Having a recent backup to role back to, in the case this happens, will be really helpful.
Please note that we did not mention important security practices, such as configuring file and folder permissions, traffic monitoring, using HTTPS instead of HTTP, or securing files through .htaccess. These methods require some knowledge, such as Unix folder structure, or Apache server configuration, that is beyond the scope of this article. Please refer to the WordPress codex for more information.
